Enterprise Scale
Secure project finance software to scale with any sized organization.




Explore Origination
Easily scale with a flexible, configurable platform
Manage end-to-end project finance process under one platform
Protect your data with the highest security standards
Empower your team to focus on the most strategic initiatives
Automated Data Collection
An integrated, single source of truth on portfolio performance.
- Improve Data Integrity and limit version control issues
- Spend the budget on strategic activities to scale, not on manually inputting data.
- Make decisions based on 360-degree visibility into your business.
- Always-on Integrations with over +30 partners across Accounting, SCADA Systems, CRM, Construction management, and other critical data sources


.webp)
Best-in-Class Workflows and Automation
Digitize workflows and drive efficiency.
- Templates allow for standardized documents and avoid duplicative efforts during document creation.
- Accelerate onboarding and deal velocity with automated workflows and checklists.
- Create standard workflows in your organization, eliminating redundant back and forth.
- Keep deals on track with collaboration and role assignment

Flexible and Configurable Setup
Configure the platform for your operations.
- Accommodate all deals and structures.
- Augment your company's unique intellectual property with best practices.
- Flexible templates, checklists, forms, and documents for your needs.
- Creating a data architecture easily aligns all future reports, documents, and data to the right investment and fund.
- Create a digital trail of the history of each transaction.


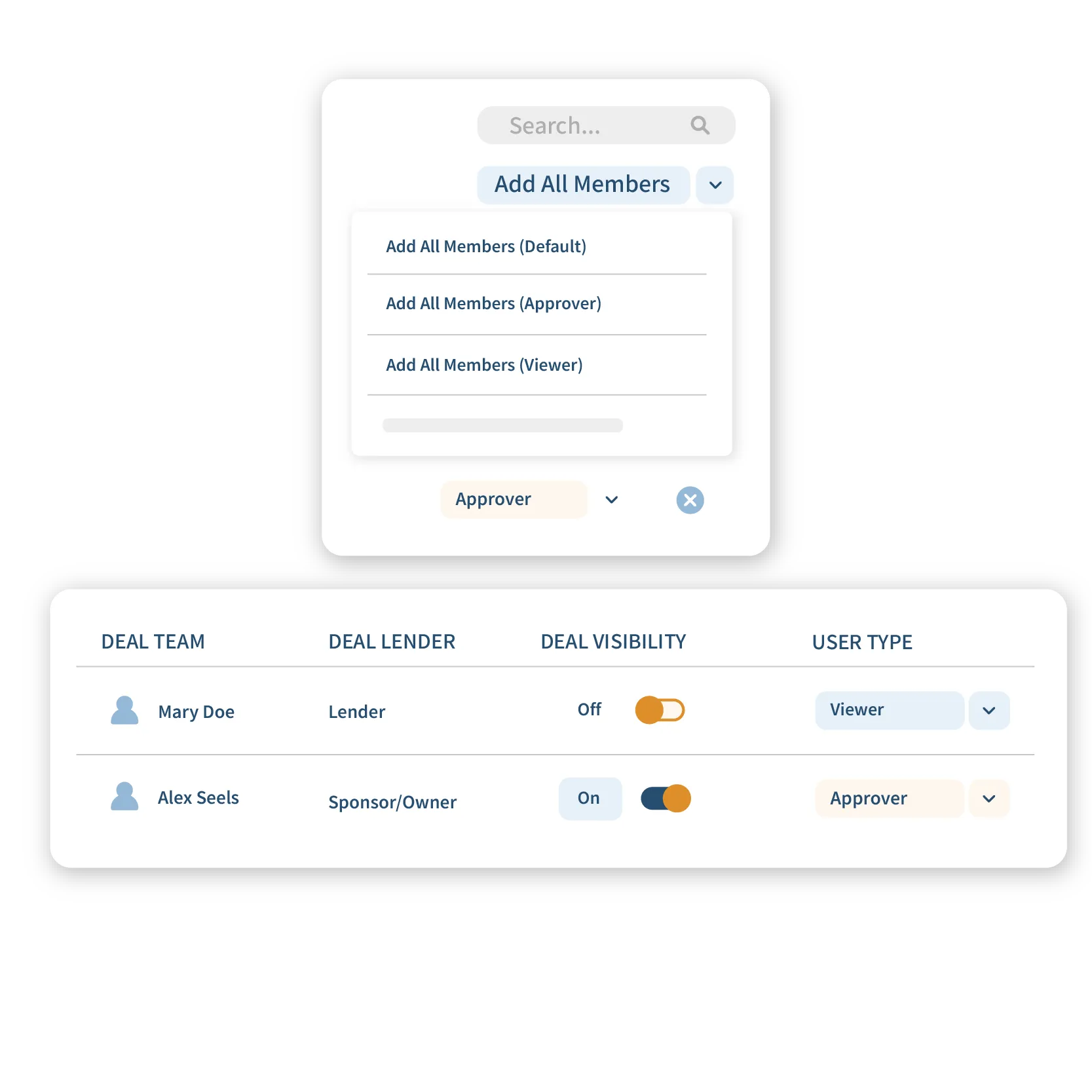
SOC2 Compliant & Enhanced Security
Enhanced security for any sized organization, giving the right access to the right people.
- Granular access control system based on user roles, granting authorized individuals the correct level of access.
- Easily onboard and verify every user with Single sign-on (SSO).
- SOC2 certification means our cloud infrastructure adheres to rigorous security standards, protecting your valuable information.
- Assign internal and guest users to deal-specific modules, data rooms, and workflows.
- Only authorized users can access crucial information.



Learn how Sumitomo Mitsui Banking Corporation uses Banyan Infrastructure to increase profitability and deal velocity
The challenge
Sumitomo Mitsui Banking Corporation (SMBC), one of the largest renewable energy portfolios in the world, was struggling to process C&I transactions in a timely manner due to inefficient workflows and manual processes, resulting in high overhead costs.
The opportunity
In order to grow their C&I business, Global Bank needed to figure out a way to accelerate deals while cutting admin and overhead costs.
The solution
By working with Banyan Infrastructure to streamline their origination process, Global Bank was able to increase deal throughput by 40% and decrease the time and overhead spent on deals, cutting 30 days from NDA to close.

With Banyan Infrastructure
- Data is centralized, up to date, and always discoverable
- Automated data collection, aggregation, and ingestion from all data sources
- Single source of truth with auditable records
- Manage your end-to-end project finance processes in one place
- Streamlined processes and automated workflows
- Efficient collaboration in a centralized workspace
Without Banyan Infrastructure
- Data is siloed, non-discoverable, with version control issues
- Manual, error-prone data entry
- Version control issues and inaccurate documentation
- Working across many different systems, with a lack of cohesiveness
- Redundant, inefficient, duplicative efforts
- Disjointed, unproductive, and inefficient collaboration
